Someone recently asked me if Microsoft’s Log Parser application could be used as a syslog agent. To be honest, I had not heard of the application so I looked it up and tried it out. This post is a result of what I learned.

What is Microsoft’s Log Parser?
From the Microsoft Log Parser page:
Log Parser 2.2 is a powerful, versatile tool that provides universal query access to text-based data such as log files, XML files and CSV files, as well as key data sources on the Windows operating system such as the Event Log, the Registry, the file system, and Active Directory. You tell Log Parser what information you need and how you want it processed. The results of your query can be custom-formatted in text based output, or they can be persisted to more specialty targets like SQL, SYSLOG, or a chart. Most software is designed to accomplish a limited number of specific tasks. Log Parser is different… the number of ways it can be used is limited only by the needs and imagination of the user. The world is your database with Log Parser.
Cool, sounds like it can handle almost any input and return almost any output!
How much does Microsoft Log Parser cost?
Free, it is available for download here.
Once you install Microsoft Log Parser, how do you use it?
Once you install and open the product you get a Log Parser command prompt with the following information:
C:\Program Files (x86)\Log Parser 2.2>LogParser
Microsoft (R) Log Parser Version 2.2.10
Copyright (C) 2004 Microsoft Corporation. All rights reserved.
Usage: LogParser [-i:<input_format>] [-o:<output_format>] <SQL query> |
file:<query_filename>[?param1=value1+...]
[<input_format_options>] [<output_format_options>]
[-q[:ON|OFF]] [-e:<max_errors>] [-iw[:ON|OFF]]
[-stats[:ON|OFF]] [-saveDefaults] [-queryInfo]
LogParser -c -i:<input_format> -o:<output_format> <from_entity>
<into_entity> [<where_clause>] [<input_format_options>]
[<output_format_options>] [-multiSite[:ON|OFF]]
[-q[:ON|OFF]] [-e:<max_errors>] [-iw[:ON|OFF]]
[-stats[:ON|OFF]] [-queryInfo]
-i:<input_format> : one of IISW3C, NCSA, IIS, IISODBC, BIN, IISMSID,
HTTPERR, URLSCAN, CSV, TSV, W3C, XML, EVT, ETW,
NETMON, REG, ADS, TEXTLINE, TEXTWORD, FS, COM (if
omitted, will guess from the FROM clause)
-o:<output_format> : one of CSV, TSV, XML, DATAGRID, CHART, SYSLOG,
NEUROVIEW, NAT, W3C, IIS, SQL, TPL, NULL (if omitted,
will guess from the INTO clause)
-q[:ON|OFF] : quiet mode; default is OFF
-e:<max_errors> : max # of parse errors before aborting; default is -1
(ignore all)
-iw[:ON|OFF] : ignore warnings; default is OFF
-stats[:ON|OFF] : display statistics after executing query; default is
ON
-c : use built-in conversion query
-multiSite[:ON|OFF] : send BIN conversion output to multiple files
depending on the SiteID value; default is OFF
-saveDefaults : save specified options as default values
-restoreDefaults : restore factory defaults
-queryInfo : display query processing information (does not
execute the query)
Examples:
LogParser "SELECT date, REVERSEDNS(c-ip) AS Client, COUNT(*) FROM file.log
WHERE sc-status<>200 GROUP BY date, Client" -e:10
LogParser file:myQuery.sql?myInput=C:\temp\ex*.log+myOutput=results.csv
LogParser -c -i:BIN -o:W3C file1.log file2.log "ComputerName IS NOT NULL"
Help:
-h GRAMMAR : SQL Language Grammar
-h FUNCTIONS [ <function> ] : Functions Syntax
-h EXAMPLES : Example queries and commands
-h -i:<input_format> : Help on <input_format>
-h -o:<output_format> : Help on <output_format>
-h -c : Conversion help
The first thing that caught my attention was the need for a <SQL query>, but who has time to RTFM? On I went looking at the examples specifically looking for one highlighting syslog:
C:\Program Files (x86)\Log Parser 2.2>LogParser -h EXAMPLES ... Send error entries in the IIS log to a SYSLOG server: LogParser "SELECT TO_TIMESTAMP(date,time), CASE sc-status WHEN 500 THEN 'emerg' ELSE 'err' END AS MySeverity, s-computername AS MyHostname, cs-uri-stem INTO @myserver FROM <1> WHERE sc-status >= 400" -o:SYSLOG -severity:$MySeverity -hostName:$MyHostname ...
OK, so basically every command requires a SQL query to process the input and send the output. Seemed simple enough so I created a file called test.txt located at C:\ and put some text in the file to ingest and send over to my Log Insight instance. Next, I constructed a Log Parser command as follows:
C:\Program Files (x86)\Log Parser 2.2>LogParser "SELECT * INTO @172.16.199.155 FROM C:\test.txt" -i:TEXTLINE -o:SYSLOG -severity:INFO -hostName:win8vm Statistics: ----------- Elements processed: 1 Elements output: 1 Execution time: 0.01 seconds
Well that was pretty easy, but did it work? Next over to Log Insight to see if my event made it over:
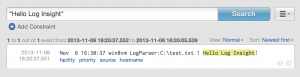
Look at that, it did! For those curious, the format of a Log Parser event appears to be: <timestamp> <hostname> LogParser:<filename> <lineNumber> <message>.
So once you get use to the syntax, it appears Log Parser is capable of sending Windows events to a remote syslog destination like Log Insight, but I did run into one major issue. While Log Parser had no problem reading a file and sending the events over syslog, I did not see an easy way for it to monitor a file and only send changes over syslog. This means Log Parser could be used for one-time troubleshooting of an application, but can not easily be used for log aggregation and correlation between systems. Now, to be fair, I did not have much time to play with the application so maybe I missed it and if I did please let me know in the comments!
Is Microsoft’s Log Parser a Windows syslog agent?
Based on my limited engagement with Log Parser, here is how I think it stacks up:
- Pros
- Can monitor any input you care about (including eventviewer, SQL, and more)
- Can output results in any format you care about (including syslog)
- Standard query language (SQL)
- Cons
- Command line only
- Not well documented
- Not well adopted in the syslog space
- Not intuitive or easy to use
- No easy ability to monitor a file for changes (I think)
- Unknown
- Resource utilization
- Performance/Speed
- Support
- Other features
- Bugs
Bottom line: Log Parser is a cool tool for one-time troubleshooting, but I would not recommend it as a Windows syslog agent. If you are looking for a Windows syslog agent, please see this post: Syslog Agents on Windows.
© 2013, Steve Flanders. All rights reserved.

It can work as an agent. This is the SQL:
SELECT TimeGenerated as TimeStamp,ComputerName as Host,EventID as Tag,EventCategory as Facility,EventType as Severity,Message as Message INTO @xxx.yyy.jjj.com:514 FROM Security where TRIM(EventTypeName) =’Failure Audit event’ AND TimeGenerated >= SUB( TO_LOCALTIME(SYSTEM_TIMESTAMP()), TIMESTAMP(’00:15:30, ‘hh:mm:ss’))
See http://forums.iis.net/t/1144985.aspx for the whole solution.
I’m stuck for the moment trying to display the resulting syslog entries properly in Log Analyzer. Info is not displayed in the proper Log Analyzer fields.
Thanks for sharing! A few comments on this method:
* I would not call this easy 😉
* I assume this only works if the log files has timestamps. If monitoring a file, this cannot be guaranteed.
* I also have doubts that this command will work with all timestamp formats like those found in files.