In my last post, I talked about the now supported VIDM integration in Log Insight. One thing I mentioned was the impact VIDM has versus LI instances with existing AD accounts. In this post, I would like to dig into the details. Read on to learn more!

AD vs. VIDM
AD is an identity provider. VIDM is an identity service. VIDM connects to identity providers including AD. Given this, you might think that a LI AD user and a LI VIDM user which maps back to the same AD user are the same — they are not. This means without a little magic, if you have a LI AD user with saved content (e.g. user alerts) and you then log in as a VIDM user which maps back to the same AD user, you will not see the same saved content as the LI AD user. The good news is LI handles this complexity for you automatically (or rather by default).
On the VIDM configuration page there is a toggle to allow AD user logins:
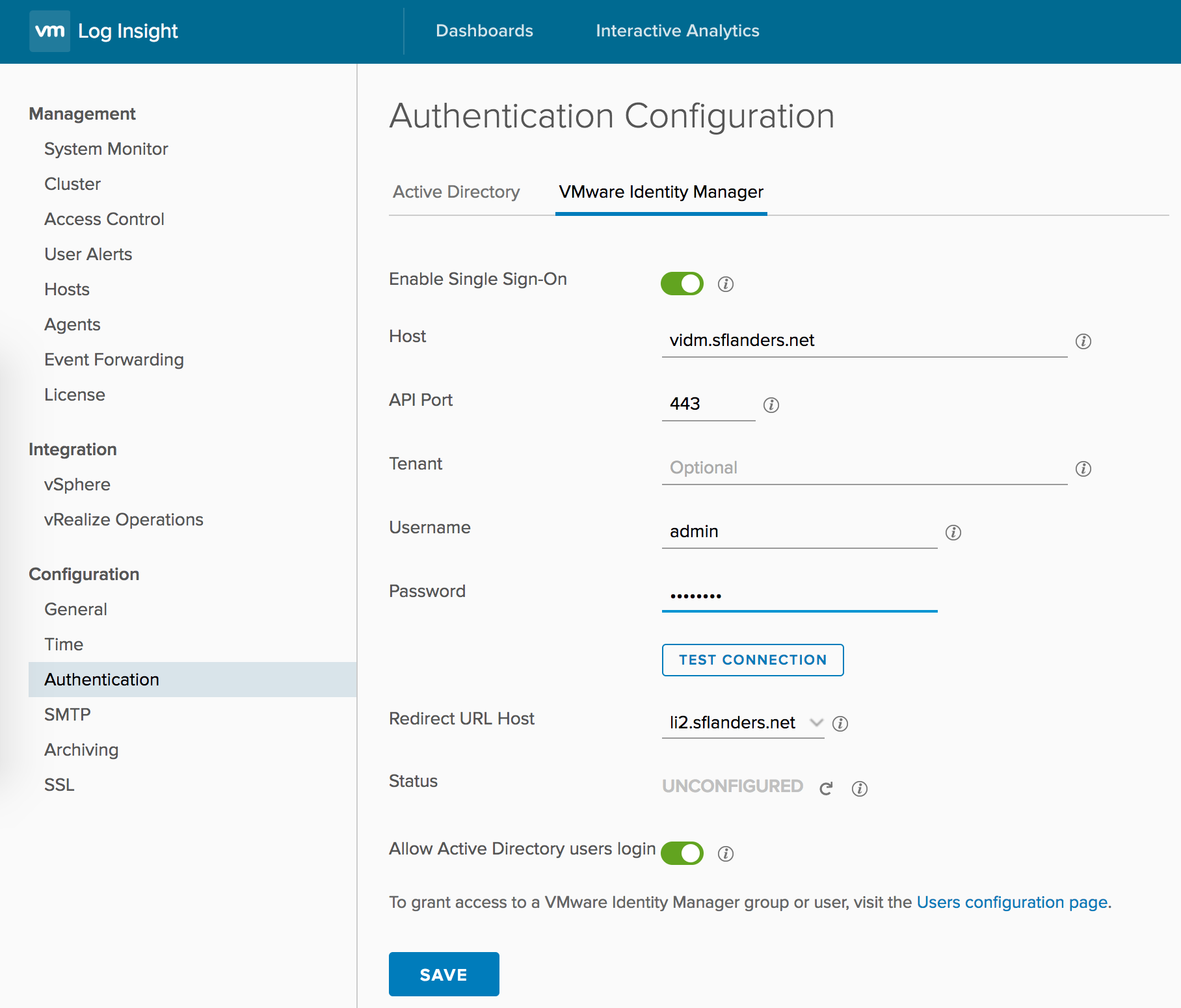
This toggle, which is selected by default, maps LI AD users to LI VIDM users (one-way). The net result is that if you have an existing LI AD user, add VIDM integration and then log in as the AD user via VIDM, you will see all the content that the AD user had saved. Now, if for some reason you do not want this behavior (please leave a comment if you have such a use-case), then you can switch off this toggle and then they will be treated as two different user accounts.
NOTE: VIDM users can be treated as AD users, but AD users cannot be treated as VIDM users. This means if you save content as a VIDM user and then wish to migrate to AD it will not work.
AD or VIDM
The answer is of course either, but in general not both. If you have both at your disposal, I would recommend VIDM over AD.
Note: As of LI 4.3, API authentication via VIDM is not supported. The supported providers are local or AD. In general, API access should be done via service accounts, but for some use-cases including using the importer with the honor_timestamp option or the query API, an actual user account may be necessary. In these cases, AD may still be needed.
The reason why not both is because there are corner cases where both can lead to issues (e.g. duplicated users). Previously, I mentioned that the allow AD user logins allowed a VIDM user to log in with the same AD user’s content. Let’s say I have the following configuration:
- A user [email protected] that exists as an AD user in LI
- [email protected] belongs to [email protected] and this group has been added to LI
- Both the user and group exist in VIDM (not LI) as VIDM connects to the same AD domain
- [email protected] is added as a VIDM group in LI
- User logs in via VIDM using [email protected]
With the above example, a new VIDM user called [email protected] will be created and it will not have the same content as the AD [email protected]. In short, the following order of operations apply when logging in via VIDM:
- VIDM users in LI trump AD users in LI
- VIDM groups in LI trump AD groups AND users in LI
This basically means VIDM can leverage AD users as well as content, but AD cannot leverage VIDM users as well as content. VIDM also provides SSO while AD does not. The future of authentication for LI is VIDM not AD.
Note: If you have an enterprise or complex AD configuration, it is strongly advised that you use VIDM.
Migrating from AD to VIDM
As mentioned above, it is not a best practice to have both AD and VIDM configured simultaneously. For those upgrading, it may be necessary to migrate from AD to VIDM. Here are the steps to migrate:
- Add VIDM integration to LI (not users or groups)
- Create a snapshot of all LI nodes
- Run a CLI script to migrate existing users
- Disable AD integration in LI
- Add VIDM groups as needed
- Modify users as needed
As mentioned in step 3, to assist with this process a CLI script is provided:
# li-convert-ad2vidm.sh
### This script should be run only once ###
id | directory_groups | name | capabilities
--------------------------------------+------------------+------------------------+------------------------------------------------------------------------------------
60258328-2845-44e3-9ae9-18331eb54f72 | null | vSphere Dashboard User | {'DASHBOARD'}
e61ad921-6fbe-457b-8206-1dc86e599c7e | null | Admin LI Only | {'ANALYTICS', 'DASHBOARD', 'EDIT_ADMIN', 'EDIT_SHARED', 'VIEW_ADMIN'}
00000000-0000-0000-0000-000000000002 | null | User | {'ANALYTICS', 'DASHBOARD'}
a88513ec-e321-477b-818f-76c0ec7be1b4 | null | View Admin | {'ANALYTICS', 'DASHBOARD', 'EDIT_SHARED', 'VIEW_ADMIN'}
5c5e6ab0-d18e-4606-99a7-a692e3a64ca5 | null | Admin No LI | {'ANALYTICS', 'DASHBOARD', 'EDIT_ADMIN', 'EDIT_SHARED', 'VIEW_ADMIN'}
fdfbcfd2-6ffc-4fee-b8fb-a1984da7d060 | null | Dashboard User | {'DASHBOARD'}
00000000-0000-0000-0000-000000000001 | null | Super Admin | {'ANALYTICS', 'DASHBOARD', 'EDIT_ADMIN', 'EDIT_SHARED', 'INVENTORY', 'VIEW_ADMIN'}
9523622b-2a4a-4c01-8fb9-eac089d8e8ed | null | vSphere User | {'ANALYTICS', 'DASHBOARD'}
### Please use a group ID from the above list for users who do not have explicitly set groups (applies to group based access users). ###
# example converting to Users group:
/opt/vmware/bin/li-convert-ad2vidm.sh 00000000-0000-0000-0000-000000000002
# example leaving the group unassigned (as is):
/opt/vmware/bin/li-convert-ad2vidm.sh null
As you can see, the script should only be run once and requires one input: the group to assign to users whose group is not explicitly set.
Note: Since you may not want all migrated users getting assigned to the same group, you may need to go to the /admin/users page and make changes to the assigned groups after running the script. This is step 6 listed above.
After providing the input, the script will run and show you the before and after of the change. For example, on a fresh LI instance which only has the admin user (meaning script will do nothing), you will see the following output:
# li-convert-ad2vidm.sh null
### This script should be run only once ###
### before conversion
0 | | admin | {00000000-0000-0000-0000-000000000001} | 00000000-0000-0000-0000-000000000002
###
### after:
0 | | admin | 00000000-0000-0000-0000-000000000002
Note: There is no going back from this change. There is no way to migrate from VIDM to AD.
Summary
VIDM is the future of authentication in Log Insight. While there are still some use-cases for AD and for basic AD environments the existing integration may be sufficient, for most production environments VIDM is the better choice going forward. Migration is possible from AD to VIDM, but remember it is a one-way migration. Try it out and leave a comment below on how it works!
© 2017, Steve Flanders. All rights reserved.
